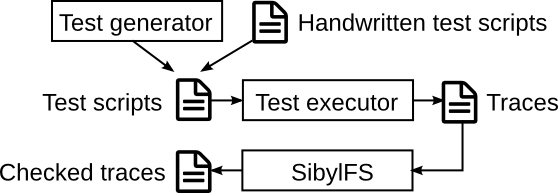
SibylFS: formal specification and oracle-based testing
for POSIX and real-world filesystems
Tom Ridge
2015-04-21
(with Thomas Tuerk, David Sheets, Andrea Giugliano, Anil Madhavapeddy, Peter Sewell; talk at Cambridge REMS meeting; 20 mins talk+10 mins qus)
Example test script
A test script is essentially a list of libc calls to execute on a real-world system
@type script
#####################################
# Test link___link_nonempty_dir1__d2__sl_dotdot_d2___nonempty_dir1__nonexist_4
#####################################
mkdir "empty_dir1" 0o777
mkdir "empty_dir2" 0o777
mkdir "nonempty_dir1" 0o777
mkdir "nonempty_dir1/d2" 0o777
open "nonempty_dir1/d2/f3.txt" [O_CREAT;O_WRONLY] 0o666
write! (FD 3) "Lorem ipsum dolor sit amet, consectetur adipisicing elit, sed do eiusmod tempor inc" 83
close (FD 3)
... // further setup commands
link "nonempty_dir1/d2/sl_dotdot_d2" "nonempty_dir1/nonexist_4"
...
Example trace (behaviour of real-world system)
A trace records the libc calls from the test script, and the responses received from the real-world system
# processing file 'link___link_nonempty_dir1__d2__sl_dotdot_d2___nonempty_dir1__nonexist_4-int.trace' ...
@type trace
#####################################
# Test link___link_nonempty_dir1__d2__sl_dotdot_d2___nonempty_dir1__nonexist_4
#####################################
5: mkdir "empty_dir1" 0o777
Tau
RV_none
6: mkdir "empty_dir2" 0o777
Tau
RV_none
7: mkdir "nonempty_dir1" 0o777
Tau
RV_none
8: mkdir "nonempty_dir1/d2" 0o777
Tau
RV_none
9: open "nonempty_dir1/d2/f3.txt" [O_CREAT;O_WRONLY] 0o666
Tau
RV_num(3)
10: write! (FD 3) "Lorem ipsum dolor sit amet, consectetur adipisicing elit, sed do eiusmod tempor inc" 83
Tau
RV_num(83)
...
28: link "nonempty_dir1/d2/sl_dotdot_d2" "nonempty_dir1/nonexist_4"
Tau
RV_none
...